Information Security Policy Images

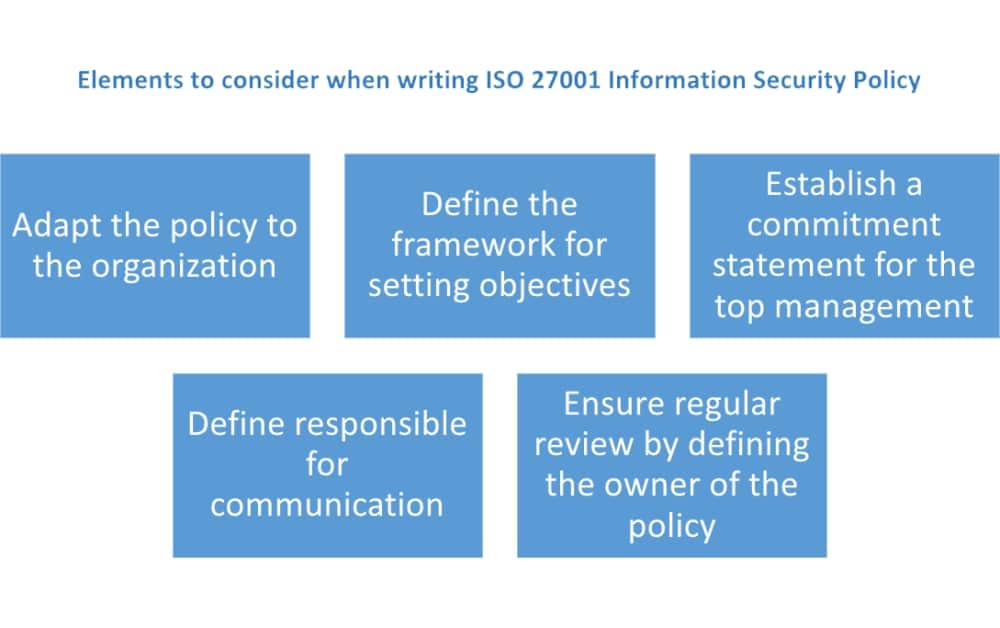
The information security policy provides an integrated set of protection measures that must be uniformly applied across jana small finance bank jsfb to ensure a secured operating environment for its business operations.
Information security policy images. Affordable and search from millions of royalty free images photos and vectors. Internet data privacy information security a computer information security and data protection concept padlock on laptop computer keyboard. 54 113 6. 379 free images of cyber security.
Technology and related supporting services policies processes and procedures that are used to create maintain secure validate assert and manage electronic identities to the ehr solution. Safe vault steel door. 220 258 62. 2 2 do s and don ts of informationsecurity.
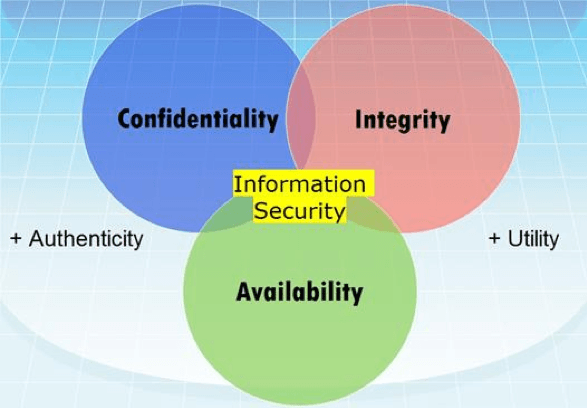
Put simply an information security policy is a statement or a collection of statements designed to guide employees behavior with regard to the security of company information and it systems etc. Download information security stock photos. Information security is a multidisciplinary area of study and professional activity which is concerned with the development and implementation of security mechanisms of all available types technical organizational human oriented and legal in order to keep information in all its locations within and outside the organization s perimeter and consequently information systems where. These security policies support the cia triad and define the who what.
Ehealth ontario ehr policy information security policy 5 identity provider services. Customer information organisational information supporting it systems processes and people. Action which breaches the terms of the information security policy and its associated policies will be dealt with via the student or staff disciplinary procedures. 5 958 free images of security.
Information will be protected against unauthorised access. Computer security protection from.